Transform Your Business with
Cloud & Security Automation


Seamless Cloud Integration with Advanced Security
Why Us?
Your Goals, Our Blueprint
Extravis doesn't just build apps, we forge pathways to success. Our team dives deep into your business goals, meticulously crafting solutions, not just applications.
Engaged Users, Better Experiences
At Extravis, beautiful interfaces are just the start. We elevate user-centric design with intuitive navigation and seamless experiences.
Tech that Transforms
Extravis builds the future with cutting-edge tech, using the latest tools to create innovative mobile apps.
Unveiling the Path to Success
At Extravis, we prioritize open collaboration with regular updates and direct communication, keeping you involved at every step.
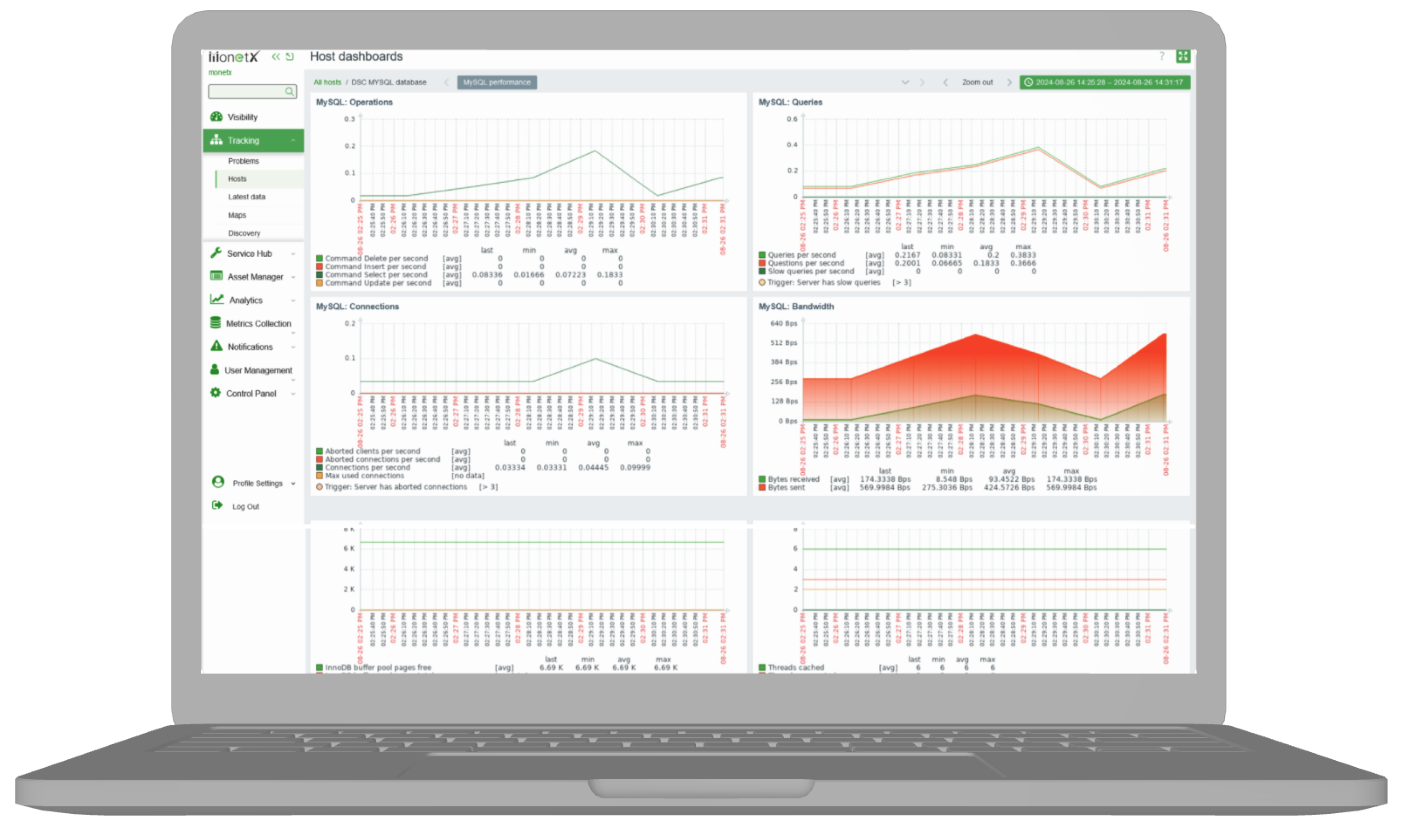
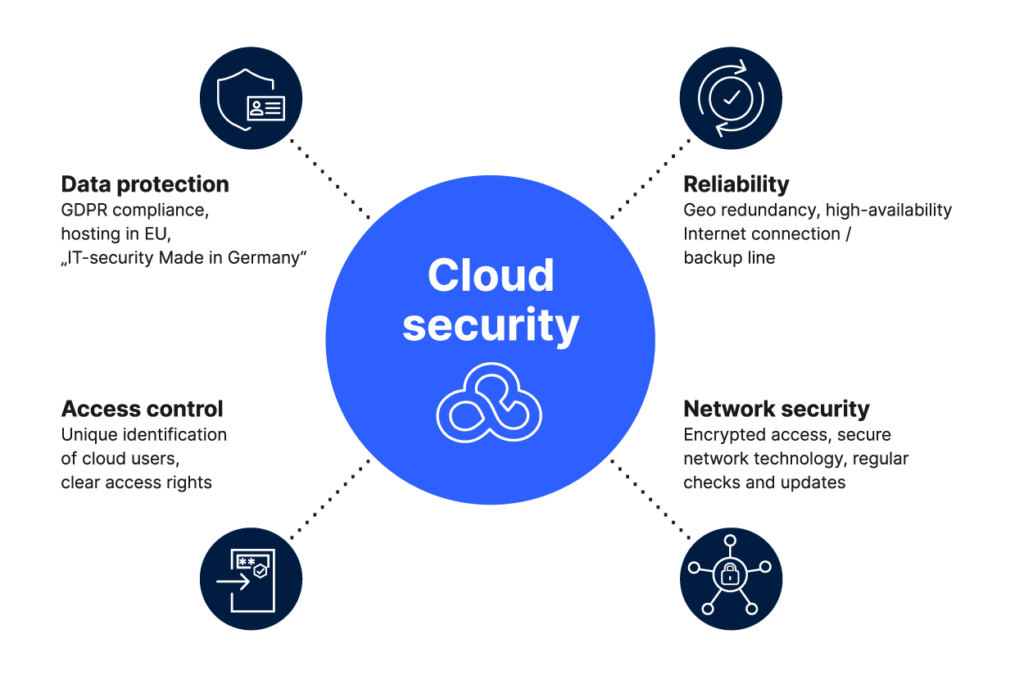
Cloud Infrastructure Security
Our tailored solutions provide continuous monitoring and protection for your cloud infrastructure. From vulnerability assessments to posture evaluations, we ensure your cloud environments meet and exceed the highest security standards.
Advanced Threat Detection
Leverage our real-time analytics and automation-powered threat detection systems to safeguard your operations. Utilizing frameworks like MITRE ATT&CK and OWASP, we detect and mitigate threats before they impact your business.
Seamless Cloud Integration
Our cloud automation integrates smoothly with your existing infrastructure, providing full visibility across hybrid and multi-cloud environments. Whether you're utilizing public, private, or hybrid clouds, our solutions streamline operations without compromising security.
Automated Compliance & Risk Management
Ensure your enterprise stays compliant with evolving regulations. Our automation solutions streamline the management of governance, risk, and compliance (GRC), reducing human error and improving response times.
Data Encryption & Access Control
Keep your data secure with multi-layer encryption and robust access control policies. We implement advanced Identity and Access Management (IAM) and zero-trust security to ensure only authorized users have access to sensitive information.
Our Technology Stack




























Get started
Ready to supercharge your business?
Grow sales and stay ahead in the competitive market by being among the first to benefit from our game-changing solutions.